About The Cyber Security Training Co
IIT Guwahati is the 6th IIT established in India. Since 1994, the institute has been at the forefront of engineering and technology education globally. This advanced certification program in Cyber Security from Intellipaat is in partnership with E& ICT Academy, IIT Guwahati. E& ICT, IIT Guwahati is an initiative of MeitY and formed with the team of IIT Guwahati professors to provide high-quality education programs.
Achievements- IIT Guwahati
You Receive An Email From Your Bank Telling You There Is A Problem With Your Account The Email Provides Instructions And A Link So You Can Log Into Your Account And Fix The Problem
What should you do?
Delete the email. Better yet, use the web client and report it as spam or phishing, then delete it.
Any unsolicited email or phone call asking you to enter your account information, disclose your password, financial account information, social security number, or other personal or private information is suspicious even if it appears to be from a company you are familiar with. Always contact the sender using a method you know is legitimate to verify that the message is from them.
Interview For Vulnerability Management Analyst Tomorrow
Hey so after many failed attempts to get my foot in the door with the Information Security department of my company, I finally have my first real shot at an in person interview with the hiring manager of the Vulnerability Management team and two senior analysts from his team.
I have done a ton of independent studying and have a few basic certs . I have not used the tools that our company uses directly , but I am familiar enough with Nessus and the concept of vulnerability scanning that I know I could get up to speed if given the opportunity. I have also spent 7+ years with the company and am pretty familiar with the organizational structure.
But I also know my technical skills and knowledege need work – I have been working in a process oriented job for about the last 3+ years, and I am nervous that I have gotten rusty.
So, that leads me to here, asking the good folks of this subreddit to lay out the type of questions you would ask a candidate for a position like this on your team? What should every good vulnerability analyst know? What would score extra points? What red flags would you look for in a candidate for an entry level / intermediate position in a role like this?
Don’t Miss: What Is Your Availability To Interview Dates & Times
What Are Spyware Attacks
Spyware is a kind of malware that is covertly installed on a targeted device to collect private data. Spyware can infiltrate a device when a user visits a malicious website, opens an infected file attachment, or installs a program or application containing spyware. Once installed, the spyware monitors activity and captures sensitive data, later relaying this information back to third-party entities.
What Do You Mean By Xss

Cross-site scripting is a type of cyberattack that injects malicious scripts into legitimate websites. XSS attacks use web applications to send these fragments of codetypically as browser-side scriptsto oblivious end users whose browsers execute the malicious script because it appears to originate from a trusted source.
Recommended Reading: How To Prepare For A System Design Interview
Is Encryption Different From Hashing
Encryption is a two-way function in which plaintext is converted into illegible ciphertext and then restored to its original plaintext form using a key. Hashing, on the other hand, is a keyless one-way function that converts information into a hash key. This hash key cannot be reversed, meaning that the original information is irretrievable.
What Is A Firewall
Firewalls are a common interview topic question in most information security interviews, including vulnerability researcher interviews. The key here is to avoid any unnecessary tangents. A firewall is a device on a network that either allows or blocks traffic based on a set of defined rules. Short and sweet wins the day here.
You May Like: How Should I Prepare For An Interview
What Do You Mean By Vulnerability
Vulnerability is the weakness of a system through which bugs or intruders can attack the entire system. In case the security testing hasnt been performed thoroughly on the system, the chances of vulnerabilities get increased.
Therefore, timely fixes or patches are needed to prevent a system from any vulnerabilities.
| If you want to enrich your career and become a professional in VAPT, then enroll in “VAPT Training“. This course will help you to achieve excellence in this domain. |
Do You Work Training Into Your Vulnerability Researcher Regimen
It is important that you let the interviewer know that not only do you work training into your vulnerability research responsibilities, but that it is essential to the position. Vulnerability researchers normally have to train current and future users of the organization on security best practices. This is due to the fact that one of the biggest causes of vulnerabilities is human error, which this training seeks to prevent.
Recommended Reading: Royalty Free Interview Background Music
What Is The Difference Between Vulnerability Management And Vulnerability Assessment
Vulnerability management is an ongoing process of securing an organizations IT infrastructure versus attack, while the purpose of vulnerability assessment projects are short-term efforts that identify your organizations immediate vulnerabilities. VA vulnerability assessment efforts and penetration tests are just one part of keeping your IT assets safe. With teams pushing code at a practically continuous cadence, CISOs can no longer only rely on point-in-time, check-the-box security testing. The increasingly dynamic and complex attack surfaces of todays digital environment require a more agile model than traditional penetration testing and more control and quality insights than other crowdsourced solutions. Because attack surfaces are constantly evolving, access to cybersecurity expertise and adversarial insights are critical to identify and resolve exploitable vulnerabilities.
IT vulnerability assessments will usually include a series of tests to determine how vulnerable your organization and its assets are. An important point to remember is that vulnerability assessments are part of vulnerability management, not a replacement. Vulnerability management, conversely, is a long-term cyclical practice that is essential for any company.
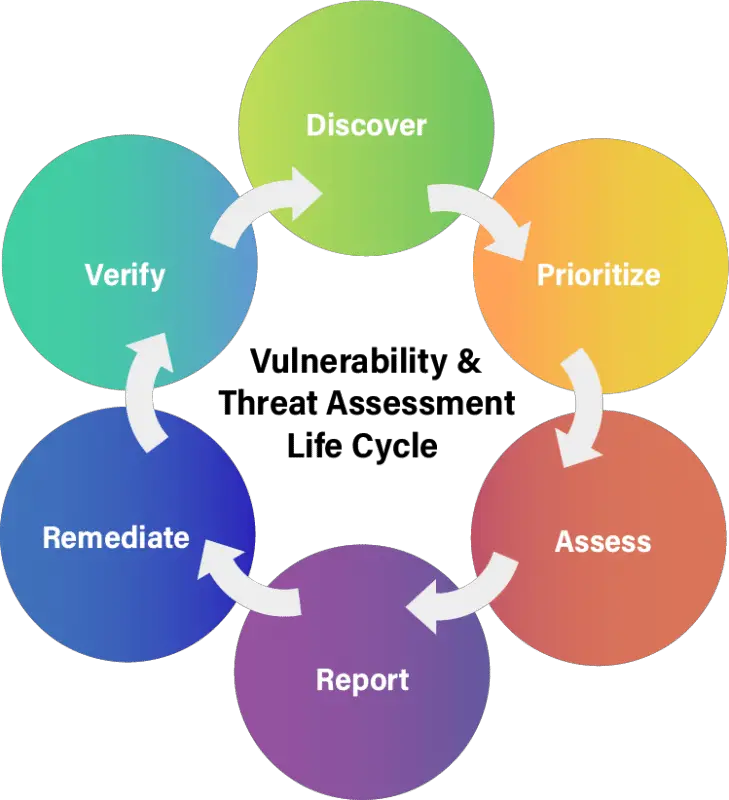
According to the SANS Institute, a long-term vulnerability management strategy contains six different components:
Why Do You Want To Build A Career In Cybersecurity
This is an opportunity to talk about the specific goals that are motivating your pursuit of a cybersecurity career. Focus your response on how these aspirations will drive you to contribute to the company, and emphasize how your career priorities will help your employer succeed. This is also a chance to assure your interviewer that the career you plan to build will involve sticking around at the company for an extended period of time. To successfully answer this question, illustrate how your passion for cybersecurity and plans for the future of your career will benefit your employer.
Recommended Reading: How To Refuse A Job Interview
Can I Attend A Demo Session Before Enrollment In This Cyber Security Course
We have a limited number of participants in a live session to maintain the Quality Standards. So, unfortunately participation in a live class without enrolment is not possible. However, you can go through the sample class recording and it would give you a clear insight about how the cyber security classes are conducted, quality of instructors and the level of interaction in the class.
A Staff Member In A Company Subscribes To Various Free Magazines To Activate The Subscription The First Magazine Asks Her For Her Birth Month The Second Magazine Asks For Her Birth Year And The Third Magazine Asks For Her Maiden Name What Do You Deduce From The Above Situation Justify Your Answer

It is highly likely that the above-mentioned three newsletters are from a parent company, which are distributed through different channels. It can be used to gather essential pieces of information that might look safe in the users eyes. However, this can be misused to sell personal information to carry out identity theft. It might further ask the user for the date of birth for the activation of the fourth newsletter.
In many scenarios, questions that involve personal details are unnecessary, and you should not provide them to any random person, company, or website unless it is for a legitimate purpose.
Recommended Reading: How To Write A Letter After An Interview
What Is Ip And Mac Addresses
IP Address is the acronym for Internet Protocol address. An internet protocol address is used to uniquely identify a computer or device such as printers, storage disks on a computer network.
MAC Address is the acronym for Media Access Control address. MAC addresses are used to uniquely identify network interfaces for communication at the physical layer of the network.
Q: If You Work With A Linux Server What Are The Three Significant Steps You Must Take In Order To Secure It
A: In order to secure your Linux server, you must do the following, in order:
- Audit. Scan the system using Lynis. Each category gets scanned separately, and a hardening index is generated for the next step.
- Hardening. Once auditing is done, hardening is done, based on the level of security to be employed.
- Compliance. This is an ongoing step, as the system is checked daily.
Recommended Reading: How To Host An Interview
Vulnerability Management: Your Questions Answered
Over the past few years, weve had news of massive data breaches within the most respected companies. In 2020, Twitter reported a breach of its platform, with captured Twitter handles being ransomed for $1000 to $2000 apiece. Fake tweets were sent out in retaliation for non-compliance. This same year, Marriott Hotels suffered a data breach, resulting in 5.2 million customers impacted.
Suffering an IT incident like this can be devastating for management and terrifying for customers. As such, its important to know how to protect yourself and your business. With that in mind, were dedicating todays blog to the topic of security and vulnerability management, and what it means for your business.
What Is The Most Useful Tool For A Vulnerability Researcher
The most useful tool for a vulnerability researcher is a vulnerability management tool. Vulnerability management is a versatile research solution that combines multiple vulnerability research functions into a single interface. Vulnerability management can give the needed edge to resolve any potential vulnerabilities more quickly than having to toggle back and forth between various different tools.
You May Like: How To Prepare For An Interview With Google
What Is The Future Of Cyber Security In The Fast
As the era is fast-moving toward better and smarter technology, cybersecurity is evidently becoming more and more threatened. It is one aspect of technology that is constantly evolving. So, there will always be a need for cybersecurity professionals to keep themselves updated on the latest threats and tools. Cyber Security defense strategies will never go away. Organizations will have to have multiple processes and technologies in place to minimize all threats and risks related to cybersecurity.
What Do You Mean By Cybersecurity
Cybersecurity is the protection of critical systems and sensitive information from digital security threats. The field of cybersecurity encompasses infrastructure security, network security, cloud security, and application security. Cybersecurity protocols are responsible for preventing security breaches that could compromise an organizations data and infrastructure. Cybersecurity encompasses security engineering and architecture, incident response, consulting, testing, and ethical hacking.
Recommended Reading: What To Know Before A Job Interview
How Does The Public Key Infrastructure Work
The working of Public Key Infrastructure at a macro level is as follows:
What Is Ssl Encryption

Secure Socket Layer is a security protocol that is used for the purpose of encryption. It ensures privacy, data integrity, and authentication in the network like online transactions.
The following are the steps for setting up an SSL encryption:
Courses you may like
Read Also: What To Expect In 2nd Interview
What Is The Difference Between Black Box Testing And White Box Testing
Black box testing evaluates the behavior and functionality of a software product. This testing methodology operates from an end-user perspective and requires no software engineering knowledge. Black box testers do not have information about the internal structure or design of the product. Conversely, white box testing is typically performed by developers to assess the quality of a products code. The tester must understand the internal operations of the product.
Explain The Osi Model
Developed in the 1970s, the OSI model is a conceptual framework that illustrates the architecture and communication functions of a network system. The model, which consists of seven collaborative layers, characterizes these functions into rules and describes how layers operate collaboratively to transmit data.
You May Like: Talent Acquisition Specialist Interview Questions
One Of The Staff Members In Xyz Subscribes To Many Free Magazines Now To Activate Her Subscriptions One Of The Magazines Asked For Her Month Of Birth Second Asked For Her Year Of Birth The Other One Asked For Her Maiden Name
What do you infer from this situation? Justify.
All three newsletters probably have the same parent company or are distributed through the same service. The parent company or service can combine individual pieces of seemingly-harmless information and use or sell it for identity theft
It is even possible that there is a fourth newsletter that asks for a day of birth as one of the activation questions
Often questions about personal information are optional. In addition to being suspicious about situations like the one described here, never provide personal information when it is not legitimately necessary, or to people or companies, you dont personally know.
What Is The Importance Of Penetration Testing In An Enterprise
Here are two common application of Penetration testing.
- Financial sectors like stock trading exchanges, investment banking, want their data to be secured, and penetration testing is essential to ensure security.
- In case if the software system is already hacked and the organization would like to determine whether any threats are still present in the system to avoid future hacks.
Don’t Miss: What To Bring To A Job Interview
Ids Vs Ips: What Is The Difference
Intrusion detection systems monitor networks for suspicious activity. When a potential threat is detected, the system will alert the administrator. Intrusion Prevention Systems are equipped to respond to threats, and are able to reject data packets, issue firewall commands, and sever connections. Both systems can operate on a signature or anomaly basis. Signature-based systems detect attack behaviors or signatures that match a preprogrammed list, while anomaly-based systems use AI and machine learning to detect deviations from a model of normal behavior.
What Are The Response Codes That Can Be Received From A Web Application
When a client sends a request to a web server, a status code is returned to indicate the response that will occur. HTTP response status codes include:
- Informational responses
- Client error responses
- Server error responses
Response codes relevant to web application security testing include: 301 , 302 , 400 , 401 , 403 , 404 , 405 , and 500 .
Recommended Reading: When To Email After Interview
What Do You Mean By Port Scanning
Ports are vital assets that are vulnerable to security breaches. Attackers use port scanning to locate open ports that are sending or receiving data on a network. This technique is also used to assess a hosts vulnerabilities by sending packets to various ports and analyzing their responses. Nevertheless, port scanning is not an inherently malicious activitycybersecurity specialists use port scanning to evaluate network security.
An Employees Bank Account Faces An Error During A Direct Deposit Two Different Offices Need To Work On It To Straighten This Out Office #1 Contacts Office #2 By Email To Send The Valid Account Information For The Deposit The Employee Now Gives The Bank Confirmations That The Error No Longer Exists What Is Wrong Here
Any sensitive information cannot be shared via email as it can lead to identity theft. This is because emails are mostly not private and secure. Sharing or sending personal information along the network is not recommended as the route can be easily tracked.
In such scenarios, the involved parties should call each other and work with ITS as a secure way of sending the information.
You May Like: How To Prepare For Technical Interview
Vulnerability Management Interview Questions
Are you thinking about how to crack vulnerability management interview questions? and how to get the best opportunity for yourself as a vulnerability management analyst? The only way to do the same is to get ready for the interview in the best way possible. Many take the interview for granted after the certification course gets over. But, the only way to have the best opportunity is to get perform well in the interview.
This is why we are here to help you with the vulnerability management interview questions that can help you become a successful vulnerability management analyst. But, before that, lets take a brief look at the field of a vulnerability management analyst and then take things ahead.