How Can You Put Separate Soft And Hard Links In Shell Scripting
Well, shell scripting is a powerful approach. The links are used when it comes to creating shortcuts just like Windows. Soft links are those which generally related to the file name and dont have any specific location. They can be anywhere on the file system.
On the other side, the hard links are related to the node and have a particular location which is fixed in most cases. They remain present on the same file system.
Explain The File System In Unix
These are a fundamental component of the file system:
- touch filename – creating/changing modification time.
- In old_name new_name – Creating a soft link on an old name.
- Is F – Displays information about the file type.
- ls -ltr – This will display in long format sorted by modified time with oldest first.
Describe Fork System Call
Ans:
The command used to create a new process from an existing process is called fork(.. The main process is called the parent process and the new process id is called the child process. The child process id is returned to the parent process and the child gets 0. The returned values are used to check the process and the code executed.
Also Check: When Do Interviews Start For Medical School
What Is The Importance Of The Gnu Project
This so-called Free software movement allows several advantages, such as the freedom to run programs for any purpose and freedom to study and modify a program to your needs. It also allows you to redistribute copies of software to other people, as well as the freedom to improve software and have it released for the public.
Q50 Can You Explain What Does The Kernel Do
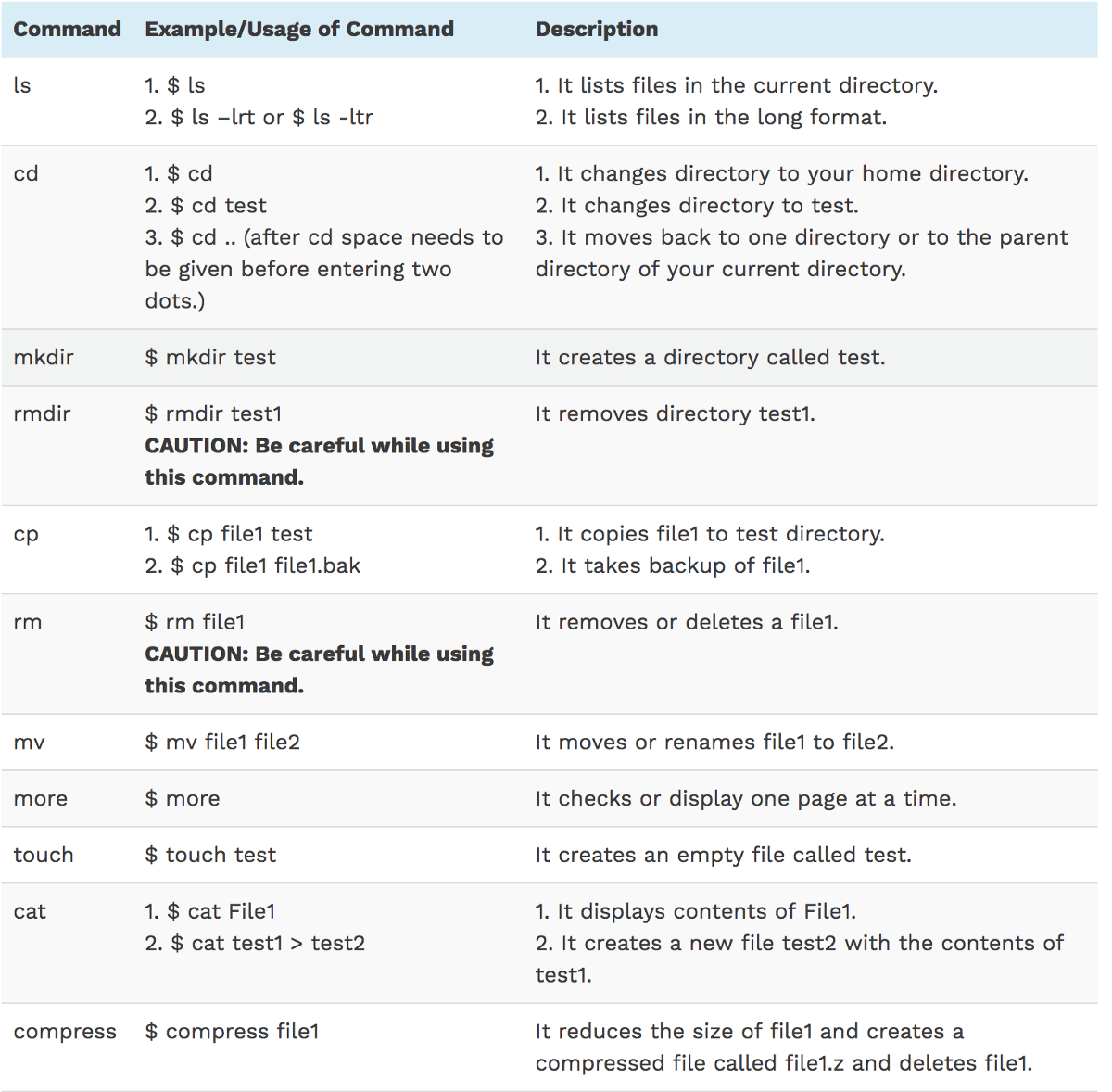
The Kernel is the heart of the operating system. It does not deal directly with the user but rather act as a separate interactive program for users logged in.
It is responsible for the following functions:
-
Interaction with the hardware
-
Debugging primitives who help programmers debug their code.
-
Support for arrays and arithmetic expressions.
-
Ability to use aliases which are defined as the shorthand names for command.
Don’t Miss: How To Write A Thank You Email Interview
How To Replace The N
This can be done in two steps. The first step is to remove the n-th line. And the second step is to insert a new line in n-th line position. Here we go.
Step 1: remove the n-th line
$> sed -i'''10 d' file.txt # d stands for delete
Step 2: insert a new line at n-th line position
$> sed -i'''10 i This is the new line' file.txt # i stands for insert
What Do You Understand By Unix Shell
Ans:
UNIX shell serves as an environment to run commands, programs, and shell scripts and also acts as an interface between the user and the Unix operating system. Shell issues $ as the command prompt, which reads input and determines the command to execute.
For Example, $date
This command will display the current date and time.
Some of the most famous shells available with Unix variants are Bourne Shell, Korn shell, C Shell.
Also Check: How To Video Interview Well
Differentiate Between Swapping And Paging
Swapping: In the case of swapping the main memory is loaded with the complete process and thus only the process less than the main memory size is executable. This is fairly easy to implement but not very efficient.
Paging: On the other hand in the case of paging instead of loading the whole process into the main memory only required memory pages are loaded. This is complex to implement but allows us to run a number of processes simultaneously.
Frequently Asked Unix And Linux Interview Questions And Answers
UNIX and Linux interview questions and answers1. How to find all the links in a folder in UNIX or Linux?tricky UNIX questionln command for creating and updating soft links
linux@nyj872:~ ls -lrttotal 2.0K-rw-r--r-- 1 Linux Domain Users 0 Dec 6 2011 adrwxr-xr-x+1LinuxDomainUsers0Sep1912:30 java/lrwxrwxrwx 1LinuxDomainUsers4Sep1912:31 version_1.0-> java/linux@nyj872:~ ls -lrt | grep '^l'lrwxrwxrwx 1LinuxDomainUsers4Sep1912:31 version_1.0-> java/
2. How to find a process and kill that?3. How to run a program in the background in UNIX or Linux?4. How to sort the output of a command in reverse order in Linux or UNIX?5. How to create an archive file in UNIX or Linux Operating System?6. What is the meaning of a file that has 644 permission?7. How will you remove empty files or directories from /tmp ?8. I have read permission on a directory but I am not able to enter it why?9. How do you find all files which are modified 10 minutes before?10. How do you find the size of a directory in UNIX or Linux?11. How do you find all the processes listening on a particular port in Linux?
$ lsof /home/someuser/somefile
Read Also: What Should Women Wear To An Interview
Explain The Kill System Call And Its Return Values
kill system call sends signals to any process which further takes suitable action according to the signal. It takes two arguments, first is PID, to which you want to send a signal and the signal you want to send is second. This method returns the following return values:
- 0 – means that the process exists with the given PID and the system allows sending signals to it.
- -1 and errno==ESRCH – means that the process/process group with specified PID does not exist
- -1 and errno==EPERM – means that the sender has no permission to send a signal to the target process.
- EINVAL – means an invalid signal was specified.
How Is Cmp Command Different From Diff Command
Ans:
cmp command is basically used for byte by byte comparison of two files to determine the first mismatch byte. This command does not use the directory name and displays the first encountered mismatched byte.
Whereas, diff command determines the changes that are to be performed on the files in order to make the two files identical. In this case, directory names can be used.
Also Check: How To Prepare Google Interview
What Are The Possible Return Values Of Kill System Call
Ans:
Kill(. system call is used to send signals to any processes.
This method returns the following return values:
- Returns 0: It implies that the process exists with the given pid and the system allows sending signals to it.
- Return -1 and errno==ESRCH: It implies that there is no existence of the process with specified pid. There may also exist some security reasons which is denying the existence of the pid.
- Return -1 and errno==EPERM: It implies that there is no permit available for the process to be killed. The error also detects whether the process is present or not.
- EINVAl: it implies an invalid signal.
Can You Explain The Method Of Changing File Access Permission

There are three components of a file permissions
- Owner permissions This determines what actions the owner of the file can perform.
- Group permissions This determines what actions a group member can perform.
- Other permissions This is for everyone else.
$ ls -l /home/sroy8091-rwxr-xr-- 1 sroy8091 users 1024 Mar 23 00:10 myfiledrwxr-xr--- 1 sroy8091 users 1024 Mar 23 00:10 mydir
r, w, and x represent read, write and execute respectively.
To change the file permission we need to run chmod command.
$ ls -l testfile-rwxrwxr-- 1 sroy8091 users 1024 Mar 23 00:10 testfile$ chmod o+wx testfile$ ls -l testfile-rwxrwxrwx 1 sroy8091 users 1024 Mar 23 00:10 testfile
Here we updated the permission for other users, from only read to read, write and execute.
Recommended Reading: What To Wear To A Teacher Interview
Q25 What Are The Various Ids In Unix Processes
A process ID is a unique integer that UNIX uses to identify a certain process.
The process executes to initiate other processes is called parent process and its ID is defined as PPID .
- getppid retrieves the Parent Process ID
Every process is associated with a specific user and is called the owner of the process. The owner has all the privileges over the process. The owner is also the user who executes the process.
Identification for a user is User ID. The process also associated with Effective User ID which determines the access privileges to accessing resources like files.
-
getpid retrieves the Process ID
-
getuid retrieves the User ID
-
geteuid retrieves the Effective User ID
Most Frequently Asked Unix Command Interview Questions
Enlisted below are the most popular and frequently asked Unix interview questions with examples.
Lets start!!
Q #1) What is a Process?
Answer: As per the definition A Process is an instance of a computer program that is being executed. We have a Unique Process Id for each process.
Example: Even when a user opens a calculator application, a process is created.
Command to list a Process: %ps
This command will provide a list of the current processes along with the process id. If we add the option ef, with the ps command, then it displays the full list of processes.
Syntax: %ps -ef
This command, when combined with the Grep, serves as a powerful means to find the particular details about a process.
Command to kill a Process: %kill pid
This command will kill the process whose process id is passed as an argument. At times using the above kill command, we wont be able to kill the process, in such a case, we will terminate the Process.
Command to forcefully Terminate a Process: %kill -9 pid
Where pid is the process id.
Another important command for listing processes is Top
Syntax: %top
Q #2) How to view your username in Unix?
Answer: You can view the details about a currently logged-in user by using the whoami command.
Syntax: %whoami
O/P test1 . It gives the user name using which you have logged in
Q #3) How to view a list of all the users who have currently logged in?
Answer: Command used is: %who.
Q #4) What is a File?
Command to list files: %ls
Example:%ls -lrt
Answer:
Don’t Miss: It Manager Job Interview Questions
What Do You Understand By Shell Variables
Ans:
A variable is defined as a character string to which a value is assigned, where values could be the number, text, filename, etc. The shell maintains the set of internal variables as well as enables deletion, assignment, and the creation of variables.
Thus the shell variables are a combination of identifiers and assigned values that exist within the shell. These variables are local to the shell in which they are defined as well as work in a particular way. They may have default value or values can be assigned manually by using appropriate assignment command.
- To define a shell variable, the set command is used.
- To delete a shell variable, unset command is used.
In Shell Scripting How Will Put Separate You The Grep And Egrep
Grep can easily be extended and the same can then be called egrep. In other words, the egrep is an advanced version of grip. There are some added features in it and i.e. it can easily be considered for the additional occurrence of a previous character. This can also be considered when it comes to alternate matching.
Recommended Reading: Oracle Cloud Infrastructure Interview Questions And Answers
Explain File Permission Groups In Linux
Ans: There are three user-based permission groups for each file and directory.
They are:
Do Your Research On The Company
Before you go in for your interview, do some background research on the company. Find out what their company mission is and some facts about their history, so you can be familiar with what they may expect of you as an employee. Doing your research can also help you come up with some questions to ask your interviewer, which can make you look interested and analytical.
Also Check: Law Enforcement Interview Room Recording Equipment
How To Check The Length Of Any Line In A File
We already know how to print one line from a file which is this:
$> sed n '< n> p' file.txt
Where < n> is to be replaced by the actual line number that you want to print. Now once you know it, it is easy to print out the length of this line by using wc command with ‘-c’ switch.
$> sed n '35 p' file.txt | wc c
The above command will print the length of 35th line in the file.txt.
Q58 How Would You Explain A Kernel To A Non

The kernel is the heart of the operating system. It is the lowest level of the operating system and is responsible for translating the command into something that can be understood by the computer. The resources allocation to different users and tasks handled by this section. The kernel doesnt have any direct communication with the user and so, it starts a separate interactive program called the shell to each user when login to the system.
You May Like: What Questions Do Interviewers Ask
Differentiate Cat Command From More Command
When using the cat command to display file contents, large data that does not fit on the screen would scroll off without pausing, therefore making it difficult to view. On the other hand, using the more command is more appropriate in such cases because it will display file contents one screen page at a time.
What Is The Zombie Process In Unix How Do You Find The Zombie Process
Zombie processes are those child processes that get finished before the parent process. So after finishing up, the process structure and address space are removed and freed back to the system but the entry in the process table still exists. To be able to get the status of the child process the parent calls wait. In the interval between the child terminating and the parent calling wait, the child is said to be a ‘zombie’.
You May Like: How To Ace A Coding Interview
Describe Key Features Of The Bourne Shell
Ans:
Bourne shell is referred to as the standard shell. The default prompt here is $ character.
The key features of the Bourne shell include:
- Input/ Output redirection.
- Use of Metacharacters for file name abbreviations.
- Using shell variables for the customizing environment.
- Creation of programs using built-in the command set.
Are You Familiar With The Methods That Are Useful In Debugging A Problem Related To The Shell Script
The answer to this question depends on the skills of a professional. There are various methods and it is not always necessary that all users consider a similar method for problem debugging. Also, it actually depends on the problem itself.
The first method that can help users to formulate the problem is simply inserting some debug statements. This will actually help the pinpoint to know how and where the problem was declared itself or reported. Another method that is also common and the users can make use of it is set-x.
Read Also: Sql Interview Questions For Data Science
How To Connect To Oracle Database From Within Shell Script
You will be using the same sqlplus command to connect to database that you use normally even outside the shell script. To understand this, let’s take an example. In this example, we will connect to database, fire a query and get the output printed from the unix shell. Ok? Here we go
$> res=`sqlplus -s username/password@database_name < < EOFSET HEAD OFF select count from dual EXIT EOF`$> echo $res1
If you connect to database in this method, the advantage is, you will be able to pass Unix side shell variables value to the database. See below example
$> res=`sqlplus -s username/password@database_name < < EOFSET HEAD OFF select count from student_table t where t.last_name=$1 EXIT EOF`$> echo $res12
Can You Tell Me Something About The Zombie Processes In Shell Scripting
These are generally defined as the scripts that have completed their life span but are yet to be picked by parent processes associated with them. In the process table, the users can locate the process id of the same despite it remains non-functional.
In some special cases, it is possible to provide the same id to the next scripts or processes when the functions performed are similar.
Don’t Miss: A Interview With God Movie
What Are The Process States In Linux
Ans: Five process states in Linux. They are
Q47 What Do You Understand By Unix Shell
The UNIX shell serves as an environment to run commands, programs, and shell scripts. In addition to that, it also acts as an interface between the user and the Unix OS. Shell issues $ as the command prompt, which reads input and determines the command to execute.
For example:$date
The command above will display the current date and time.
You May Like: How To Prepare For Software Development Manager Interview
Who This Course Is For:
- Software Engineer, Sr. Software Engineer, Member Technical Staff, Expert
- Operations Engineer, DevOps Engineer
- Anyone who wants to learn Unix interview questions
- 3.8 Instructor Rating
- 31,071 Students
I am a Software Architect with expertise in Cloud Computing, Amazon Web Services, Microservices, Data Science, Hadoop, Spark, Machine Learning and Java architecture. Learning, using and sharing Technology is my passion.I have built systems that are running enterprise software of companies across the world. I have gained a lot of knowledge by working hands-on on these large scale software projects.With these courses I aim to share my knowledge with the future Software Engineers, Developers, Leaders and Architects . I am sure the knowledge in these courses can give you extra power to win in life.All the best!!