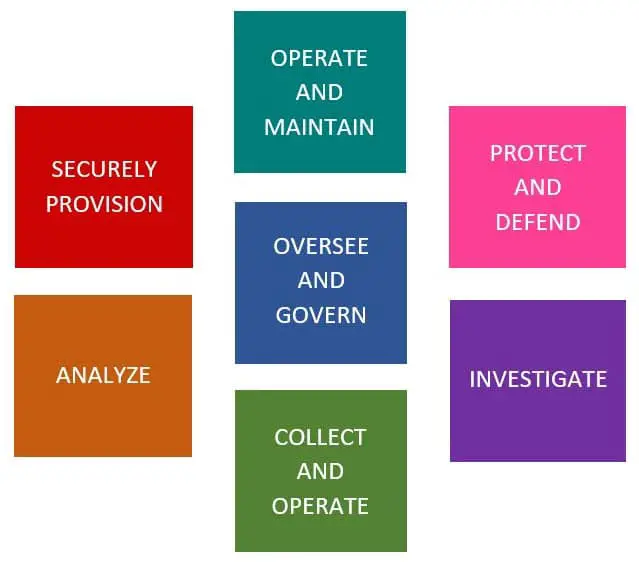
Nist Cybersecurity Framework: A Cheat Sheet For Professionals
The US National Institute of Standards and Technology’s framework defines federal policy, but it can be used by private enterprises, too. Here’s what you need to know.
The tech world has a problem: Security fragmentation. Theres no standard set of rules for mitigating cyber riskor even languageused to address the growing threats of hackers, ransomware and stolen data, and the threat to data only continues to grow.
SEE: NIST Cybersecurity Framework: A cheat sheet for professionals
President Barack Obama recognized the cyber threat in 2013, which led to his cybersecurity executive order that attempts to standardize practices. President Donald Trumps 2017 cybersecurity executive order went one step further and made the framework created by Obamas order into federal government policy.
The framework isnt just for government use, though: It can be adapted to businesses of any size.
TechRepublics cheat sheet about the National Institute of Standards and Technologys Cybersecurity Framework is a quick introduction to this new government recommended best practice, as well as a living guide that will be updated periodically to reflect changes to the NISTs documentation.
SEE: All of TechRepublics cheat sheets and smart persons guides
Is There An Approval Process To Purchase Applications I Find That Would Be Useful For My Work
Most companies do have policies about how to purchase software . It is important to know which applications you can use immediately, and which may need further investigation to ensure they are secure enough for your use and the data that will be processed and/or stored within them. Know what is required and work with your cybersecurity professional to go through the required processes to ensure the information will be secured properly.
If you would like to better understand your cybersecurity risk, you can use the MEP National NetworkTM Cybersecurity Self-Assessment Tool. If you have questions or would like to speak to a cybersecurity professional, connect with your local MEP National Network Center.
Shoppers With A 05% Conversion Rate For A Chair That Costs $250 Wayfair Makes A 27% Profit Next 50000 Shoppers Will Get A 10% Discount What Is The Conversion Rate They Must Achieve To Achieve The Same Profits As Before
This is incorrectOld revenue = 50000*250*.005=250*250New revenue with conversion rate r% = 50000*r*250*.9 = old revenue = 250*250r = .55%Less
July 9 is wrong because the profit margin changesLess
The new conversion rate is 0.944, Profit from case 2 = $16,875and the third part, if this scenario actually occurred I would give a 10% discount because the overall profit margin would remain same i.e. $16,875Less
Recommended Reading: How To Ace Google Interview
How Long Does It Take To Learn Cybersecurity
To launch a cybersecurity career, youll need to build the necessary technical skills through a degree program or a tech bootcamp. If you pursue a bachelors degree or masters degree in computer science, information system management, or engineering, youll need to set aside two to four years of studyplus time to prepare for cybersecurity certification exams.
If you choose to learn cybersecurity through a high-quality bootcamp program, you can finish the course in six months working at approximately 15-20 hours per week. A strong bootcamp program will also incorporate preparation materials and offer official practice exams to help you earn a cybersecurity certification.
With the right curriculum and one-on-one guidance from an industry expert mentor, youll be able to build the cybersecurity skills you need to get hired.
Since youre hereInterested in a career in cybersecurity? With or Cybersecurity Bootcamp, youll get a job in the industry, or well return your tuition money. Test your skills with our free cybersecurity learning path, and check out our student reviews. Were a safe bet.
About Sakshi Gupta
Sakshi is a Senior Associate Editor at Springboard. She is a technology enthusiast who loves to read and write about emerging tech. She is a content marketer and has experience working in the Indian and US markets.
Hids Vs Nids: Are They The Same
HIDS are host-based intrusion detection systems while NIDS are network-based intrusion detection systems. Because HIDS can detect malicious data packets originating from within the enterprise network, these systems are useful for catching inside threats. HIDS reviews historical data to identify unconventional cyberattacksunusual host-based actions changes to system files will trigger an alert. NIDS, however, detect threats in real-time through live data tracking of network traffic, meaning NIDS can catch hackers before a complete system breach occurs.
You May Like: How Can I Watch Meghan Markle Interview
How Do You Differentiate Between Viruses And Worms
While viruses attach to a file or program, worms exploit network vulnerabilities to enter a network. Viruses only replicate when activated by a host, and will remain dormant in a system until an action is taken to trigger execution. Conversely, worms propagate independently after breaching a system and can spread without human interaction or the assistance of a host.
Questions To Use For Self
The Baldrige Cybersecurity Excellence Builder can be used as a guide to craft a thoughtful questionnaire. It categorizes questions by subject matter and offers guide questions for each category.
The following will present general, flexible questions for each category. This list is by no means complete, as a good self-assessment considers all aspects of an organizations cybersecurity posture and needs to fit the organization as much as possible. Accordingly, a solid self-assessment should fill out this questionnaire outline with hand-crafted questions that apply to the organizations specific cybersecurity posture and needs.
These questions can be found in the Baldrige Cybersecurity Excellence Builder,here.
You May Like: How To Perform Well In An Interview
What Is The Difference Between Diffie Hellman And Rsa
- Diffie-Helman: Its a key exchange protocol where two parties exchange a shared key that either one can use to encrypt/decrypt messages between them.
- RSA: Its asymmetric key encryption where it has two different keys. The public key can be given to anyone and decrypted with another, which is kept private.
Related Article: Cyber Security Best Practices
How Long Would You Wait Before Deploying A Critical Update
There are two schools of thought about critical updates. One is that any update that is considered critical needs to go out immediately to prevent any further damage. The other is that we must wait to ensure that the cure doesnt cause more problems than what its fixing. In either scenario, we want a test environment to ensure everything works as expected before deploying to production whenever possible.
I say whenever possible because 90% of the time, this is the responsible thing to do especially if the product we are patching may not have the best track record for updates being all good right out of the gate. Sometimes we have to wait for the update to the update to the update to the hotfix before it actually does what its supposed to do. However, the other 10% of the time, something in our environment DEMANDS this fix, and we desperately need it right now.
We also need a way to revert out of it, though, if things go utterly sideways.
You May Like: Why Should I Hire You Interview Question
Which Is More Secure Ssl Or Https
- SSL is a secure protocol that provides safer conversations between two or more parties across the internet. It works on top of the HTTP to provide security.
- HTTPS is a combination of HTTP and SSL to provide a safer browsing experience with encryption.
- In terms of security, SSL is more secure than HTTPS.
What Is A Siem
SIEM is Security Information and Event Management software that provides a holistic view of what is happening on a network in real-time and help cybersecurity analyst to be more proactive in the fight against security threats.
SEM security event management carries out analysis of the event and logs data in real-time to provide event correlation, threat monitoring, and incident response
SIM security information management retrieves and analyses log data and generate a report. For the organization that wants complete visibility and control over what is happening on their network in real-time, SIEM solutions are critical.
How Does SIEM work?
SIEM collects log and event data that is generated by host systems, security devices, and applications throughout an organizations network infrastructure and collating it on a centralized platform. From antivirus events to firewall logs, SIEM software identifies this data and sorts it into categories, such as malware activity, failed and successful logins, and other potentially malicious activity.
When software identifies activity that could signify a threat, alerts are generated to indicate a potential security issue. These alerts can be set either low or high priority using pre-defined rules.
SIEM solutions provide a powerful method of threat detection, real-time reporting, and monitoring, long term analytics of security logs and events.
Don’t Miss: How To Prepare For Pm Interview
Can You Explain Tcp Three
The TCP three-way handshake is the method used in a TCP/IP network to create a connection between a local host/client and server. It is a three-step method that requires both the client and server to exchange SYN and ACK packets before actual data communication begins.
A client node sends an SYN data packet over an IP network to a server on the same or an external network. The objective of this packet is to ask/infer if the server is open for new connections.
The target server must have open ports that can accept and initiate new connections. When the server receives the SYN packet from the client node, it responds and returns a confirmation receipt the ACK packet or SYN/ACK packet.
The client node receives the SYN/ACK from the server and responds with an ACK packet. Upon completion of this process, the connection is created and the host and server can communicate.
Cybersecurity Is An Organizational Problem Not Just A Technical Problem
Many cybersecurity problems occur because of human error. A study from Stanford University revealed that 88% of data breach incidents were caused by employee mistakes. Aligning all employees, not just the cybersecurity team, around practices and processes to keep the organization safe is not a technical problem its an organizational one. Cybersecurity requires awareness and action from all members of the organization to recognize anomalies, alert leaders, and ultimately to mitigate risks.
Our research at MIT suggests this is best done by creating a cybersecurity culture. We define a cybersecurity culture as an environment infused with the attitudes, beliefs and values which motivate cybersecurity behaviors. Employees not only follow their job descriptions but also consistently act to protect the organizations assets. This does not mean that every employee becomes a cybersecurity expert it means that each employee is held accountable for overseeing and behaving as if he or she was a security champion. This adds a human layer of protection to avoid, detect, and report any behavior that can be exploited by a malicious actor.
Read Also: Spring Boot Interview Questions For 10 Years Experience
Whats Your Ideal Next Step
We all have our dreams and desires, and often we try to fit what we want into someone else’s container because we don’t see the right container in front of us, Clark says. When we can get a well thought-out answer to this question, it can open up possibilities and opportunities that may not have been obvious before.
People change jobs to get closer to feeling as if they are living out their purpose, Clark says, and companies should want to know as much about that purpose as possible in order to ensure there is a right match, particularly in when making critical hires.
More on the CISO role
Why Is Cybersecurity In Demand
First and foremost, cyberattacks are costlyin fact, data breach costs rose to $4.24 billion per incident in 2021. As a result, many companies are investing in cybersecurity to skirt revenue loss and maintain customer trust. Digital transformation has touched every industry, and assets ranging from online financial transactions to industrial IoT-enabled machinery are now vulnerable to exploitation. As a result, cybersecurity regulations are growing, motivating organizations to protect their data and stay up-to-date with evolving legislative mandates.
Also Check: What Questions They Ask In A Job Interview
Black Hat Hackers Vs White Hat Hackers Vs Grey Hat Hackers: Are All Illegal
Black hat hackers use cybersecurity knowledge to gain unauthorized access to networks and systems for malicious or exploitative ends. This type of hacking is illegal. Conversely, white hat hackersalso known as ethical hackersare hired to evaluate the vulnerabilities of a clients system. Because white hat hackers operate with the permission of their targets, this activity is legal. Grey hat hackers may search for system vulnerabilities without permission, but instead of exploiting the vulnerability directly may offer to fix the issue for a price. Because the intrusion was not permitted, grey hat hacking is often considered unethical and illegal.
What Is Referred To As A Man
A man-in-the-middle attack occurs when a bad actor interferes with communications between two parties and monitors or manipulates the traffic traveling between them. Man-in-the-middle attackers are able to passively eavesdrop on the connection or actively intercept the connection in order to reroute traffic to another destination. The goal of such attacks may be to steal information or corrupt data, among other motivations.
You May Like: Formal Attire For An Interview
What Is Global Teaching Assistance
Our teaching assistants are a dedicated team of subject matter experts here to help you get certified on your first attempt. They engage students proactively to ensure the course path is being followed and help you enrich your learning experience from class onboarding to project mentoring and job assistance. Teaching Assistance is available during business hours.
Implementing The Nist Framework Core
Cybersecurity based on the NIST Cybersecurity Framework can be a challenge. Regardless of how challenging it could be, it will be worthwhile, though. Given that the Framework is based on outcomes rather than specific controls, it allows organizations to build from a strong foundation and supplement to achieve compliance with new regulations as they emerge. The core functions: identify, protect, detect, respond and recover, aid organizations in their effort to spot, manage and counter cybersecurity events in a timely manner. The NIST CSF cybersecurity approach will help empower continuous compliance and support communication between technical and business-side stakeholders.
CyberStrong has unmatched access for NIST Cybersecurity Framework mappings and is customizable to controls you define. To learn more about CyberStrong, contact us.
Read Also: Buyer Real Estate Agent Interview Questions
What Do You Mean By A Vpn
A virtual private network establishes a protected network connection when using a public network. A VPN can encrypt internet traffic in real-time, thereby securing data that travels across the network and preventing third parties from tracking user activity. VPNs redirect a users IP address through a remote host server, allowing for IP address concealment.
What is the difference between VA and PT ?
Vulnerability assessments identify and report security weaknesses in system architectures. Penetration testing strives to exploit those vulnerabilities and determine the extent to which a cybercriminal could compromise an organizations assets.
What Are Intrusion Detection Methods Explain Them

The intrusion detection system is a device or software that monitors a network or systems for malicious activity any violation is reported to the SIEM system. IDS types can be host-based and network-based. IDS can detect a malicious activity based on a signature-based approach or anomaly-based approach or a combination of both.
Read Also: What To Write In A Thank You Email After Interview
Is A Ceh Certification Worth It
The CEH certification is a pioneer in setting a global standard for ethical hacking. The EC-Council works to deliver only the latest technologies such as container technology, OTT technology, and involves hands-on hacking challenges as well. The credential is trusted by many Fortune 500 companies like Cisco, Ford Motors, IBM, Microsoft, Verizon, Citi bank, and more. Take our CEH training to add this globally recognized credential to your portfolio and become a successful ethical hacker.
Distinguish Among Threat Vulnerability And Risk
Threat:
Classifying something as a threat should have potential and adverse effects on the company that could cause damage to the computer system, including the network, server, or company as a whole. A threat can appear in any form as an individual, technology in a malware form, or even natural disasters.
Vulnerability:
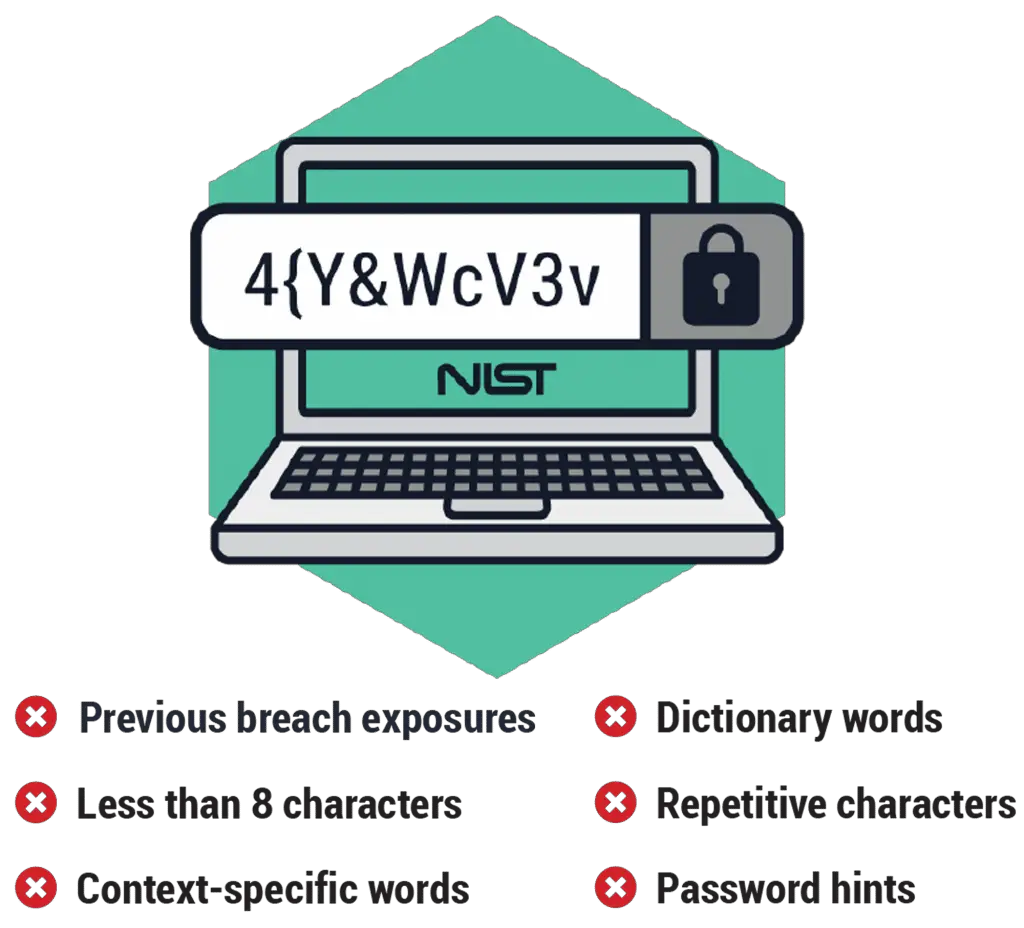
This can also take many forms, such as an unpatched server, weak passwords, an open port on an unmonitored computer on your network, etc. Vulnerability is a gap in the system security protocols which is an open gate for various attacks and breaches. Cybercriminals can use this to gain unauthorised entry, thereby causing security breaches.
Risk:
The worst-case scenario is the risk that can happen when a threat is carried out against vulnerability on the network. This is potential damage to the company and is used to help motivate any security-related issues to be detected, prevented, or corrected.
Recommended Reading: What Is Cloud Computing Interview Questions And Answers
What Is Vlan What Is The Difference Between Vpn And Vlan
VPN: it is related to remote access to a network with a secured and encrypted tunnel. Saves the data from prying eye while in transit and no one on the net can capture the packets.
VLAN: Helps to group work stations that are not within the same locations into the same broadcast domain. Logically segregates networks without physical segregation with switches. Does not involve any encryption.
What Are Encoding Hashing And Encryption
Encoding: Converts the data in the desired format required for exchange between different systems.
Hashing: Maintains the integrity of a message or data. Any change did any day could be noticed.
Encryption: Ensures that the data is secure and one needs a digital verification code or image in order to open it or access it.
Also Check: How To Reject Applicant After Interview